So just what is the Heart Bleed OpenSSL bug? To put it n layman’s terms many servers use OpenSSL cryptography library for encrypted TLS connections i.e. SSL connections. This allows users to safely transmit data between there PC’s and servers using an encrypted connection. It allows a layer of security to protect your confidential data.
Many services use this type of connection like your email providers (Google, Yahoo) banking institutions and service providers like DropBox, SEMRush to name a few.
Well the HeartBleed bug is a vulnerability in this type of connection and specifically in the OpenSSL cryptography library. To put it mildly, hackers can now see transmitted information and even access secure server connections to download sensitive information! This vulnerability has actually been around for the last 2 years but has only come to the forefront when it was publicly announced on 1st April 2014 by the Google security team. Since then many service providers have been clambering to update their OpenSSL libraries to fix the bug. The infographic below (courtesy of the security watch team @ PCMag) shows how the vulnerability works:
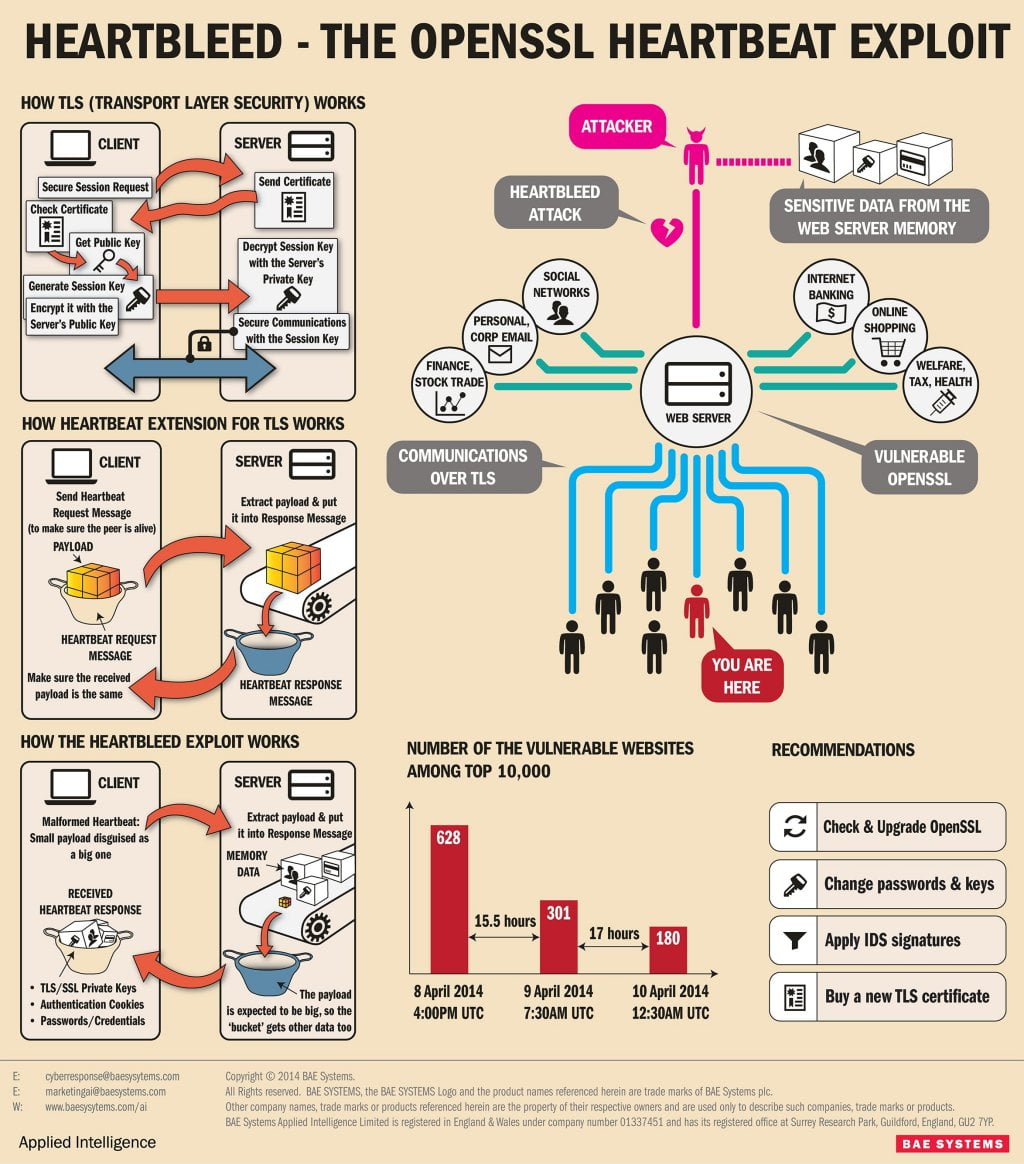
The bug was named by a finish cybersecurity company which also designed the heart bleed logo and published a website: http://heartbleed.com/ explaining to the public what the heart bleed bug was.
What services have been affected by the Heart Bleed OpenSSL Bug?Amongst the many services that have been widely affected are email services, social networks, ecommerce stores and various service providers. Also, Google’s popular Android platform seems to be affected by the vulnerability but according to many industry experts, the platform will not be targeted until the ‘easier’ targets have been saturated. This, however, gives little comfort considering there are over a billion devices that may be affected by running the Android platform, from smartphones to tablet devices the bug could leave you vulnerable. A comprehensive list of what services and companies that are affected can be found here: http://mashable.com/2014/04/09/heartbleed-bug-websites-affected/
So what can you do to protect yourself? And how do you know that you are vulnerable? Many of the affected providers have now updated there OpenSSL libraries. However, as a precaution, they are also advising their users to change passwords as a precaution. Only recently SEMRush and DropBox have sent out emails to their users advising them to change their passwords as a precaution. There is also now an abundance of services popping up that will check if you are vulnerable to the HeartBleed bug. The most favoured service we have found is from a company called McAfee. A well-known company that provides many security products with the best known McAfee internet security that you can find in many retail shops. It’s an easy to use HeartBleed checker tool that allows you to check if your server is affected by simply typing in the website URL. Its quick and easy to use.
There is also a number of apps you an now download from Google Play to your Android device to check if your android device is effected. This one s provided courtesy of TrendMicro (a big name in internet security) The Trend Micro Heartbleed Detector scans your Android mobile device for possible risk and helps you stay away from the Heartbleed bug.
What does Heartbleed Detector check on your mobile device?- Whether your mobile device is affected by the Heartbleed bug
- Whether applications on your mobile devices are affected by the Heartbleed bug
- Whether applications on your mobile devices access a cloud service that is affected by the Heartbleed bug
You can Download the App Now via Google Play.
Now for the good news. Umbrella Host and all its servers and services are not vulnerable to this bug. We take the security of our data including our clients very seriously. As such we always implement regular updates to our servers to ensure that any vulnerabilities are quickly fixed. Keeping our servers up to date not only allows us to provide quality services but ensures that our users data is also protected.


